To utilize the single sign-on with ADFS, you’ll need a properly configured SAML 2.0 compliant identity provider with properly configured relying party trust in ADFS.
This MS documentation should be able to help in setting that up: https://docs.microsoft.com/en-us/powerapps/maker/portals/configure/configure-saml2-settings
Notes:
The relying party identifier is: https://www.reftab.com/
The SAML Assertion consumer endpoint is: https://www.reftab.com/api/sso
Binding: POST
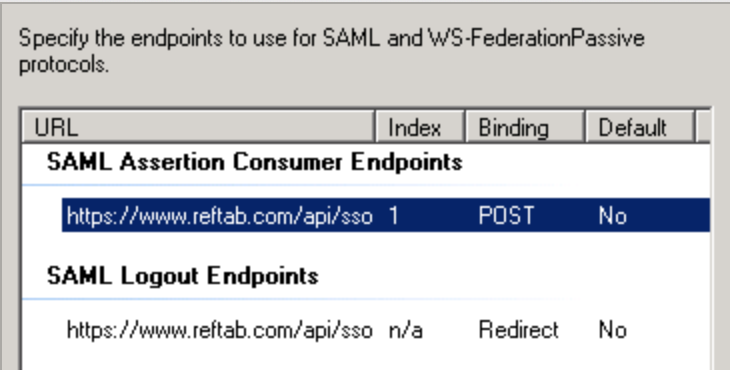
Once done, you’ll need to setup claim rules: You’ll need to click “Add Rule” and go through the wizard to configure a claim for the email attribute at the least:
- Click Add Rule.
- In the Claim rule template list, select the Send LDAP Attributes as Claims template, and then click Next.
- Create the following rule:
- Enter a descriptive rule name
- Attribute Store: Active Directory
- Add the following mapping
- LDAP Attribute: E-Mail-Addresses
- Outgoing Claim Type: E-Mail Address
- Click OK.
- Create another new rule by clicking Add Rule, this time selecting Transform an Incoming Claim as the template.
- On the next screen, create the following rule:
- Enter a descriptive rule name
- Incoming Claim Type: E-Mail Address
- Outgoing Claim Type: Name ID
- Outgoing Name ID Format: Email
- Pass through all claim values (the default)
- Finally, click OK to create the claim rule, and then OK again to finish creating rules.
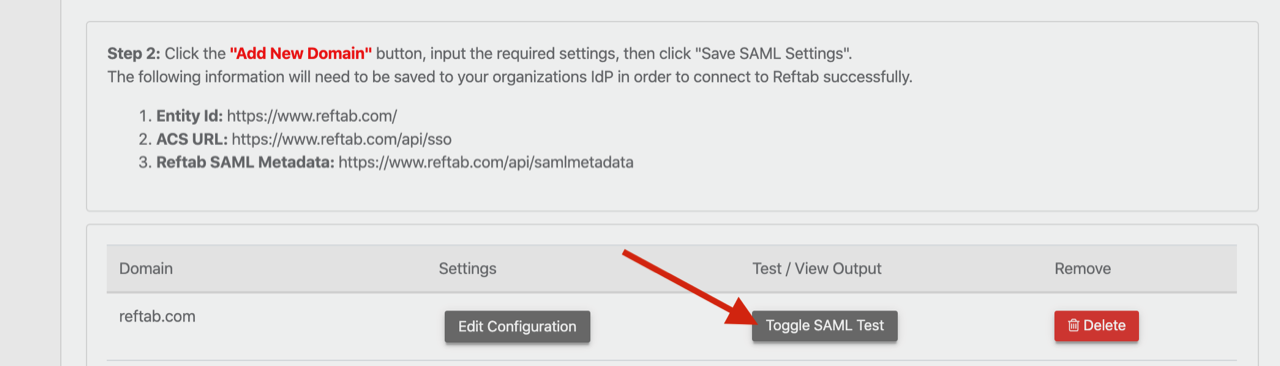
Once this is done, you will also need the certificate so that you can add it into Reftab. Within Reftab, click “Settings” > “SAMLSettings” > “Add New Domain“
You will need to provide to Reftab:
- Domain Name
- IDP Entity ID
- URI Endpoint
- Bind Method
- Attribute to Identify Users
- Attribute to Identify Users Name (optional)
- Certificate
- Encryption Certificate.
Once it is done and saved, you can click “Toggle SAML Test” to run a test connection:
The test will succeed if you see attributes exposed with an attribute name and a value column.
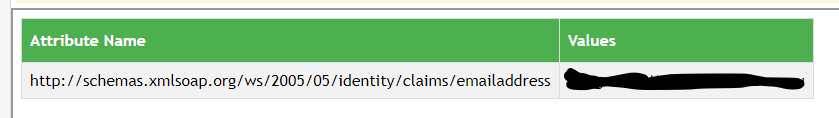
If you see an error such as:
“Error Attribute for user email not found make sure settings are correct in Reftab SAML Settings Attribute found: “http://schemas.xmlsoap….”
Copy the attribute that was found and use that for the Attribute to Identify Users in Reftab then save and test again.